Control access with proof & precision
Share what matters while protecting what's sensitive with precision data controls.


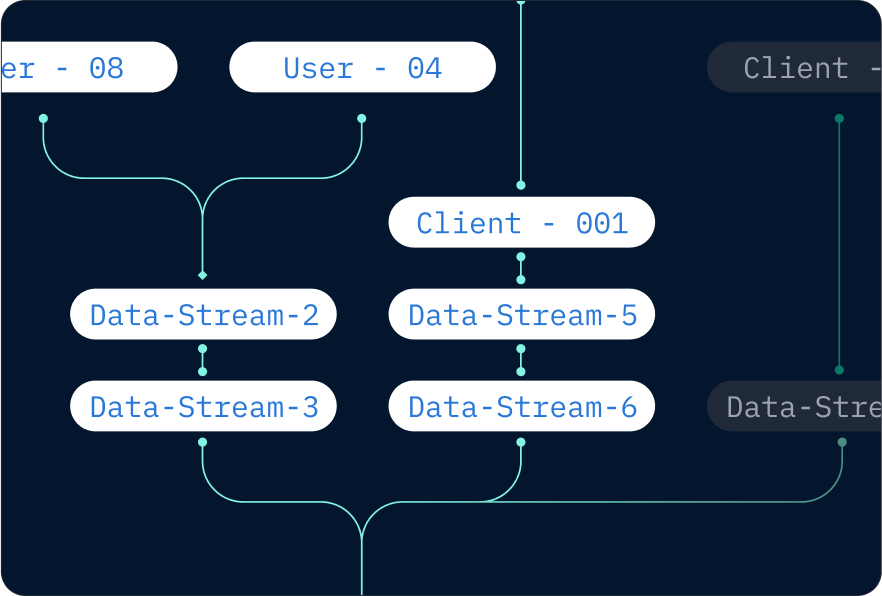
Decide who sees what with controlled data access
Protect sensitive information with controlled data access, full traceability, and a verifiable audit history.
Granular permissions
Set precise access levels for each user or team, ensuring they have exactly the rights they need—no more, no less.
Version control
Track every change with a complete, verifiable history, so you always know what was updated, when, and by whom.
Automated backups
Store critical data in secure, redundant locations with rollback options to recover instantly from loss or corruption.
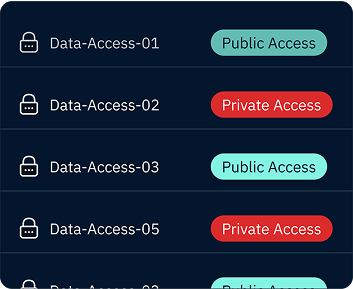
Take control of your data with granular access management
Share verified information while keeping confidential details private, all while maintaining a complete record of data interactions.
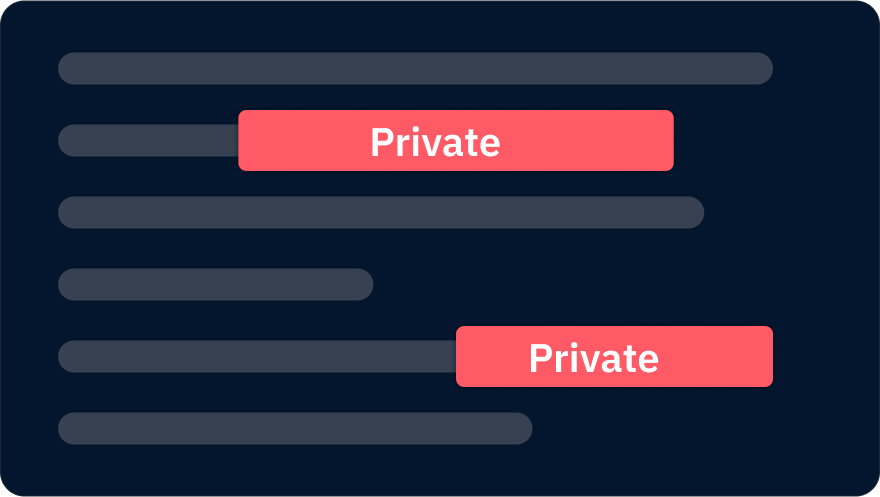
Enhanced security
Protect your sensitive information with advanced protection layers that defend against unauthorized access while enabling legitimate sharing.
Streamlined workflows
Automate permission management and data sharing processes to reduce administrative burden and improve operational efficiency.
Flexible integrations
Connect your existing systems with our platform to create a seamless data security environment across your entire organization.
Take control of your data
With granular access management and full traceability. Let’s talk about your goals.
See what our clients say
“Techflow X is an exceptional app that stands out!”
Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisinostrud aliquip ex ea commodo consequat excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id.
“Techflow X is a top-of-the-line app with amazing features!”
Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisinostrud aliquip ex ea commodo consequat excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id.
“Filedgr is the new standard for verifiable data.”
"We chose the Filedgr DAO Fund structure as it provides a unique European birthmark to our issued token. Filedgr's data attestation platform convinced us with its products that foster full transparency, something essential in today's digital asset marketplace.”

Controlled data access solutions for modern enterprises
Filedgr creates secure exchange pathways that enable verification. You control what's shared, with whom, and for how long. Only the verification information they need, with full visibility into how that information is accessed.